Blackshades Net Can Best Be Described as a Bot
RAT Bot Wrapper DDoS Tool. BlackShades Net can best be described as a.
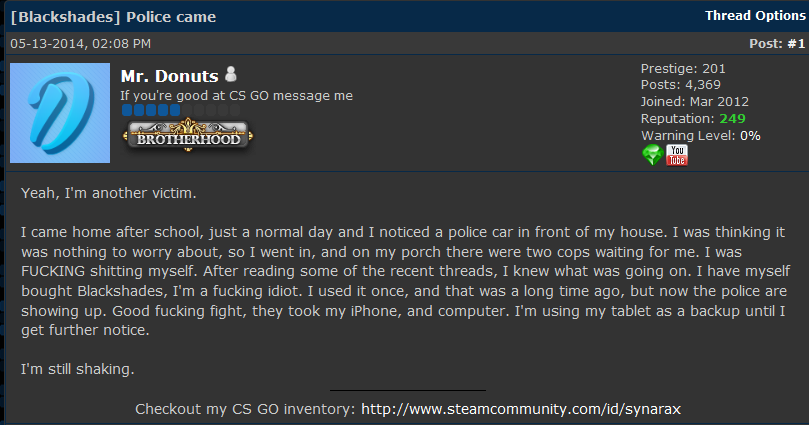
Blackshades Trojan Users Had It Coming Krebs On Security
Dameware Mini Remote Control.
. 1 BlackShades is a Remote Access Tool or RAT. However the only one we. BlackShades Net can best be described as a.
Its 100 legal for you to install spy software on your own computer. Question 73 1 point. The top means of infection by BlackShades is via Skype instant messages which attempt to infect new victims by portraying BlackShades as a safe video file in the pif format.
A 24-year-old Swedish man. An analysis of the notorious Blackshades remote administration tool which was at the center of a global criminal network found the toolkit rich. The two types of honeypots include.
According to a report by CNN the cost to buy the malware called Blackshades on the cyber black market can be as little as 40. Due to the fact that most legitimate RATs require a user to. DDoS Tool RAT Question 80 0 1 point Buffer overflow attacks allow an attacker to modify the _____ in order to control the process execution.
Although RATs have many legal uses and are sold by software companies they can also be used for malicious purposes such as data theft spying and distributed denial of service attacks. Raids took place in more than a. Here are the 5 things you need to know.
She was a victim of Blackshades. Blackshades is a remote administration tool RAT used for remotely accessing and controlling computers over the internet. Choose all that apply Question 73 options.
The software is sued to remotely take over computers and can be used to access the computers hard drive log key strokes in order to capture passwords and can even turn on the webcam without the computer users knowledge. Theres a Trojan infection that is being used in the Syrian governments suppression of its countrys political dissidents. Main part of the Spy Act is about adware and spyware related software and website which use to gather user information for advertisement.
As a threat to your ability to control your PC or safeguard it against privacy invasions BlackShades should be removed quickly and by the application of the best anti. The BlackShades website offers a variety of products which can help to accomplish the goals listed above. One of the creators of BlackShades 21 year old Michael Hogue aka xVisceral was arrested for not only credit card cybercrime but also for the advertising and selling of malware namely the RAT BlackShades.
More than 100 people worldwide have been arrested following an FBI-led crackdown on hackers linked to a remote administration tool called Blackshades. Once installed it allows a. In 2014 the United States Federal Bureau of Investigation arrested hundreds of.
This malware allows a remote user to access an infected computer granting hackers access to data information about user activity and control over peripheral devices like webcams. Blackshades is one of the many malicious tools targeting Internet-connected computers that even a novice can use. In recent attacks the BlackShades Trojan has deployed.
Which of the following is an Internet Relay Chat bot. Blackshades is a malicious trojan horse used by hackers to control infected computers remotely. Bot Wrapper RAT DDoS Tool Question 6 5 points Question 6 Unsaved DDoS Sim features include which of the following.
An interesting note is that xVisceral had announced his. Question 73 1 point With Cross Site Scripting attackers can inject malicious ____. Brute Force Attacks Guessing Dictionary Attacks Hybrid Attack Question 5 5 points Question 5 Unsaved BlackShades Net can best be described as a.
Bot Wrapper DDoS Tool RAT Question 73 1 point With Cross Site Scripting attackers can inject malicious ____. According to US officials over 500000 computer systems have been infected worldwide with the software. Choose all that apply Question 4 options.
JavaScript HTML VBScript Flash Question 74 1 point. BlackShades is the name of the operation responsible for the distribution of a malicious remote administration tool RAT used to take control of infected machines. It targets Windows-based operating systems and allows the cyber criminals using it to take control of.
So what is BlackShades and why is this being called the largest ever international cyber crackdown. Directory Traversal BlackShades Net can best be described as a. Choose all that apply Question 73.
This Trojan known as BlackShades is a Remote Access Tool RAT that allows the attacker command the infected PC from a remote location. He threatened to post the photos online. The malware targets computers using operating systems based on Microsoft Windows.
Bot Wrapper DDoS Tool RAT. Question 72 1 point BlackShades Net can best be described as a. Access end-users computers laptops and servers for remote administration and support.
A 20-year-old kid named Jared James Abrahams used Blackshades to take nude photos of Wolf and others through their webcams. High interaction According to your text most of the webservers run which of the following. IPS IDS low interaction.
Explicit session ID Cloned session Hash BlackShades Net can best be described as a. Question 78 0 1 point BlackShades Net can best be described as a. The forum itself was in essence a honeypot for cybercrime activities.
Not replying to SYNACKs A flaw in how the three-way handshake can be implemented A flaw in some firewalls which do not restrict ICMP traffic by default.
The Truth About Blackshades Malware Fixedbyvonnie
The Truth About Blackshades Malware Fixedbyvonnie

Comments
Post a Comment